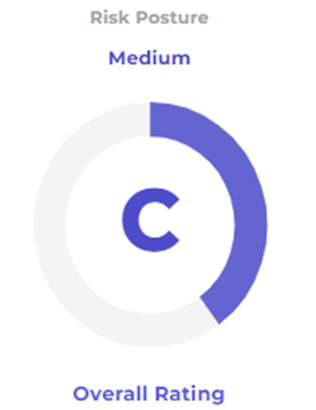
External Cyber Score
Third Party Risk Management
- Evaluation of suppliers using questionnaires and qualitative approaches is old school approach. Cyber Risk is dynamic in nature, agility in supplier governance from risk assessment and mitigation leveraging automation is the need of the day
- Also, the risks of third-party vendors are not only a problem for your company, but also your customers making it a problem for the entire Ecosystem.
- With our External Cyber Score, you can stay ahead of the game with third-party cyber risk monitoring service and strengthen your organization’s ecosystem posture.
Brand Monitoring
- The more you know about cybercrime, the more you can do to help protect your brand.
- External Cyber Score monitors your brand, products/services, executives and connected with ongoing cybercrime campaigns. With our automated 24x7 security monitoring service, you can stay on top of the latest cyber threats.
Stay on top of your external cybersecurity posture
A proactive monitoring service that works 24x7 to help you stay on top of rising threats
- Be proactive, not reactive: When it comes to cybersecurity, your company's external digital assets are often overlooked. It is important to know how attractive you look to the hackers – to have a “Hacker View”
- Our service External Cyber Score discovers all your external digital assets and provides you with a hacker's view. This enables you to detect all vulnerabilities and assess the potential risks
- Our service also helps you gather all leaked credentials on a continuous basis to help you mitigate the risk of cybercriminals abusing the leaked credentials for Phishing attacks, which is the topmost attack vector today
- We leverage our partner Cyfirma’s capabilities to monitor over 200 million domains and social media profiles for impersonation, infringement, and data breach risks. It also alerts you to new threats appearing on the web.
- We will warn you of new vulnerabilities and risk exposure that could be exploited by hackers.
Hacker view of external assets
External Cyber Score
- Regular scanning of external digital assets exposed to cyber criminals
- Continuous reporting of vulnerabilities as visible to cyber criminals
- Ecosystem view by extending the external score to suppliers and customers
- Benchmarking with competitors
- Continous checks on compliance with various IT security standards
- Non-instusive approach without touching the network on assets of the potential customer
Key Features |
|||
| Ecosystem View | Vulnerabilities mapped to various standardards ISO, GDPR | ||
| Non-intrusive approach | Minimizing the risk of cyber attacks and criminal activities | ||
| Expert consultants to guide on the cyberscore results | |||